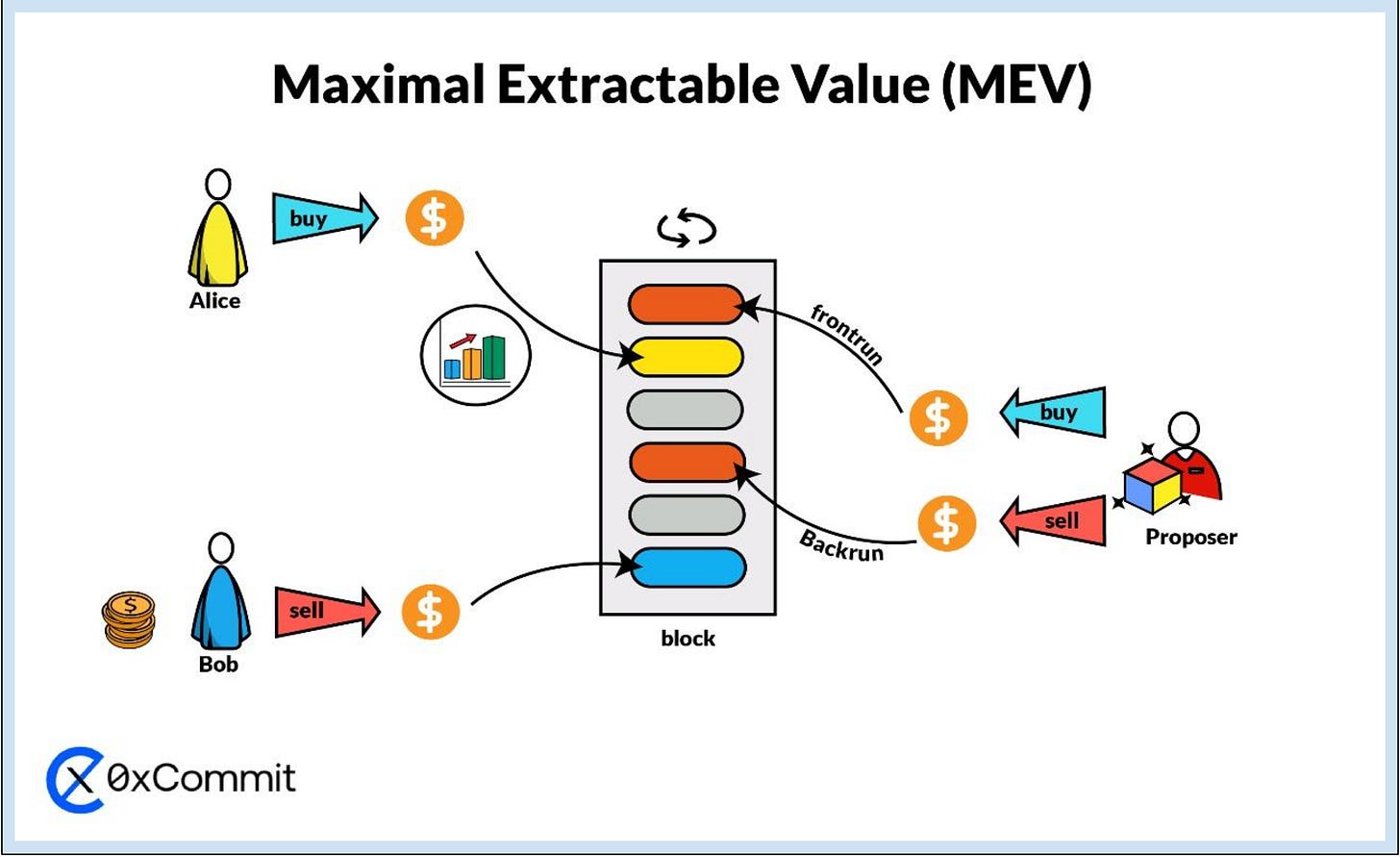
Maximal Extractable Value (MEV) refers to the potential profit that can be extracted by miners or validators through their control over the ordering of transactions within a blockchain block. Initially, MEV focused on the potential for miners to extract additional value from transaction ordering and manipulation, particularly before the Ethereum network transitioned to its proof-of-stake (PoS) consensus mechanism.
1. History and Evolution of MEV
MEV has its roots in the early days of Ethereum, where it was originally termed "Miner Extractable Value." In this early context, MEV referred to the additional profit miners could gain by manipulating the order of transactions within a blockchain block. This practice allowed miners to prioritize or reorder transactions to extract extra value beyond the standard transaction fees.
As Ethereum and other blockchain networks developed, the scope of MEV expanded significantly. The rise of decentralized finance (DeFi) and the proliferation of complex smart contracts introduced new dimensions to MEV strategies. These advancements enabled more sophisticated forms of value extraction, reflecting the growing complexity of the blockchain ecosystem.
Initially, MEV strategies were relatively straightforward, focusing primarily on direct financial gains from the ordering of transactions. However, the introduction of DeFi and innovative financial products brought about more intricate MEV tactics. This evolution marked a shift from simple transaction manipulation to advanced strategies involving complex interactions between smart contracts and financial mechanisms.
2. Post-Merge MEV Landscape in Ethereum
The transition from Ethereum's proof-of-work (PoW) to proof-of-stake (PoS) consensus mechanism, known as "The Merge," marked a pivotal change in the blockchain's architecture. This shift has not only altered how Ethereum secures its network but also how MEV is conceptualized and exploited.
Prior to The Merge, MEV, also known as Miner Extractable Value, was primarily associated with the ability of miners to manipulate transaction ordering within blocks to maximize their profits. Miners, through PoW, had direct control over transaction prioritization, which often led to unfair practices and inefficiencies.
Post-Merge, Ethereum transitioned to PoS, which brought about several key changes in the MEV dynamics:
2.1 Validator Centralization
In PoS, validators take over the role previously held by miners. They validate blocks and participate in consensus by staking ETH. However, with the minimum staking requirement of 32 ETH, many individuals opt for staking pools to participate. This can lead to centralization, where a few large validators control a significant portion of the network. This concentration of power poses a risk as these large validators might exert disproportionate influence over transaction ordering and MEV opportunities, potentially worsening the centralization and fairness issues in the network.
2.2 Permissioned Mempools
To counteract MEV-related attacks such as sandwiching and front-running, permissioned mempools are being considered. These mempools restrict access to transaction data, allowing only selected parties to view and submit transactions. While this approach can reduce the scope for MEV exploitation by limiting who can see and act on pending transactions, it introduces new challenges. It could compromise Ethereum's permissionless nature, transforming it into a “pay-to-play” system where only those who can afford to pay for transaction privacy benefit, exacerbating centralization concerns.
3. How Does MEV Work?
MEV arises from the discretionary power that block producers have over transaction ordering within a block. This power enables them to extract additional value by strategically selecting and ordering transactions, beyond the basic transaction fees.
3.1 Transaction Pool and Selection
When users submit transactions to a blockchain network, these transactions enter a staging area known as the mempool (memory pool). The mempool holds unconfirmed transactions until they are picked up by block producers to be included in the next block. Block producers have the autonomy to select which transactions from the mempool they will include. While transaction fees typically guide this selection, block producers are not obligated to follow this pattern.
3.2 Transaction Ordering and MEV Extraction
The core of MEV extraction lies in the ordering of transactions within a block. Since each block has a limited capacity, the order in which transactions are processed can significantly affect their value. Block producers can manipulate transaction order to maximize profits by leveraging various MEV strategies. For instance, they might prioritize transactions with higher fees or reorder transactions to exploit arbitrage opportunities.
3.3 Impact on Users
MEV extraction can adversely impact regular users, sometimes in ways that are not immediately obvious. For example, users might experience worse price execution for their trades if block producers exploit MEV opportunities at their expense. This aspect of MEV underscores the broader implications for fairness and efficiency within blockchain networks.
4. MEV Strategies
MEV involves various sophisticated strategies employed by miners, validators, or other actors to optimize their profits. Below is an extensive exploration of the primary MEV strategies, including front-running, back-running, and sandwich attacks, with detailed descriptions of each:
4.1 Front-Running
Front-running is a strategy where a participant places a transaction ahead of an observed pending transaction in order to capitalize on anticipated market movements. This tactic exploits the ability to control the order in which transactions are included in a block.
Mechanism: In this approach, when a significant trade is detected in the mempool (a holding area for unconfirmed transactions), a front-runner submits their transaction with a higher fee to ensure it is processed first. This is done to benefit from the price movement that the large trade is expected to trigger.
Example: Suppose a large buy order for a cryptocurrency is waiting to be processed. A front-runner identifies this and places their own buy order with a higher fee, ensuring it is executed before the large trade. As a result, the price of the cryptocurrency increases, allowing the front-runner to sell their assets at a higher price and realize a profit from the price increase.
4.2 Generalized Front-Running
Mechanism: This advanced form of front-running utilizes complex algorithms and machine learning models to analyze transaction patterns across the network. Bots are employed to scan the mempool and predict profitable opportunities based on observed transaction data.
Example: A sophisticated bot detects patterns in transaction data that indicate a forthcoming significant price movement. The bot executes its trades in advance of this predicted movement, thereby capitalizing on the anticipated price changes before other market participants can react.
4.3 Back-Running
Back-running involves placing a transaction immediately following a significant transaction to take advantage of the price movement or other effects caused by the initial transaction.
Mechanism: The back-runner strategically positions their transaction to benefit from the impact of the preceding significant transaction. This strategy exploits the changes in market conditions resulting from the initial transaction.
Example: After a substantial buy order pushes up the price of a token, a back-runner executes a sell order to profit from the price spike created by the initial trade. By timing their transaction right after the significant trade, they are able to benefit from the resulting price increase.
4.4 Sandwich Attacks
Sandwich attacks are a manipulation strategy that involves placing two transactions around a target transaction to exploit price fluctuations or other market changes caused by the target transaction.
4.4.1 Basic Sandwiching
Mechanism: In this type of attack, the perpetrator places a buy order before the target transaction to drive up the price, allows the target transaction to execute at this inflated price, and then places a sell order to capture the profit from the price increase.
Example: The attacker identifies a large order that will influence the price of an asset. They place their buy order before the target transaction to push the price up, let the target transaction execute at this new price, and then sell their assets at the elevated price to make a profit from the price change.
4.4.2 Pool Imbalance Sandwiching
Mechanism: This variant of sandwiching involves manipulating liquidity pools during the front-run and back-run phases to exploit the target transaction. By altering the liquidity distribution, the attacker can disadvantage the target trade.
Example: The attacker adjusts the sizes of liquidity pools before and after the target transaction. This manipulation can result in the target trade receiving minimal or no return, effectively squeezing the value out of the transaction.
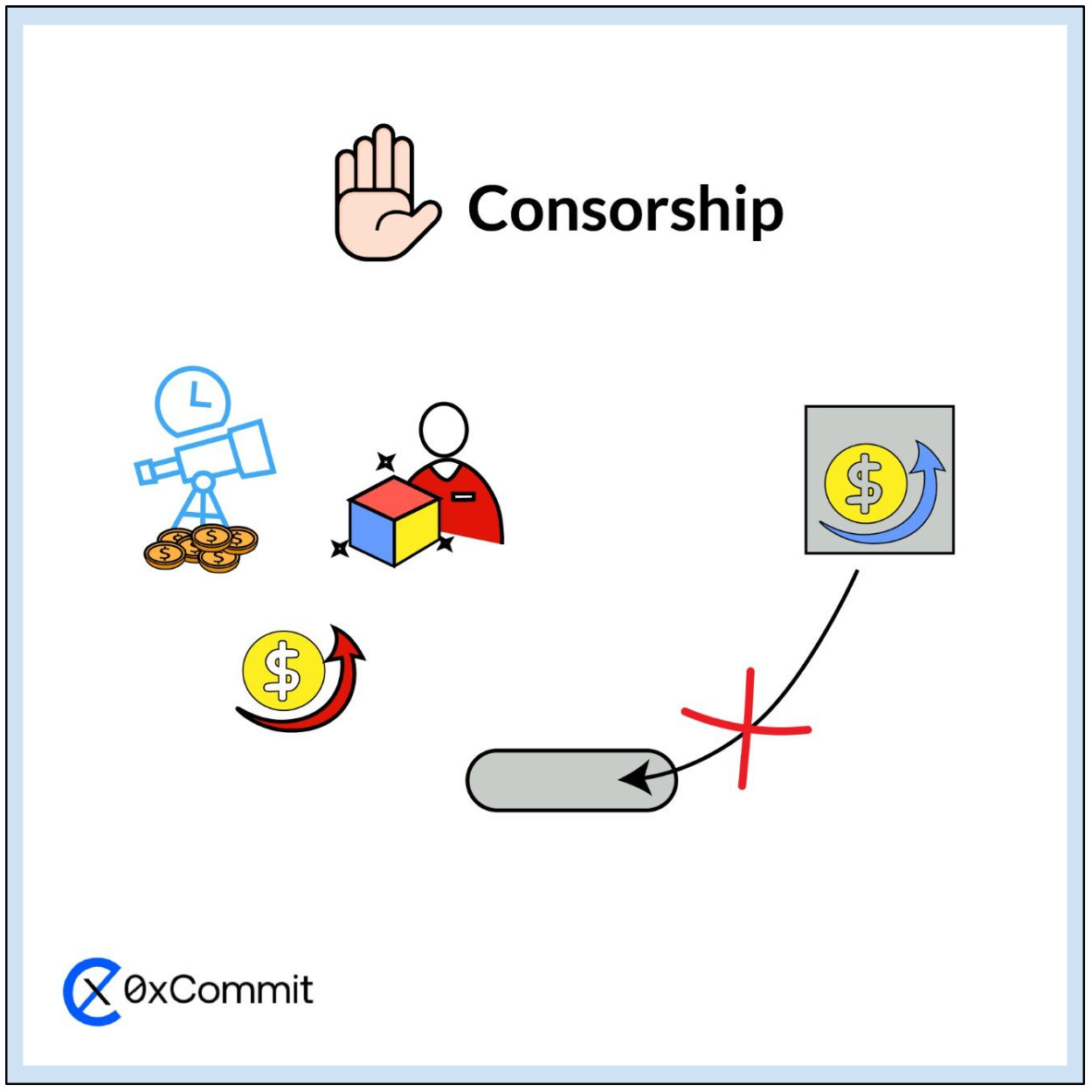
4.5 Censorship
Censorship in the context of MEV involves intentionally excluding specific transactions from a block to gain a competitive advantage or maintain an arbitrage opportunity.
4.5.1 Transaction Censorship
Mechanism: This strategy involves miners or validators deliberately omitting certain transactions from inclusion in a block. The aim is to prioritize their own transactions or those of their affiliates, thus distorting the fairness of the blockchain.
Example: A miner might exclude transactions from a competitor’s trading bot to ensure that their own transactions or those of their clients are prioritized for inclusion in the block. This creates an uneven playing field and undermines the fairness of the transaction processing system.
4.6 Arbitrage
Arbitrage refers to the practice of exploiting price differences of an asset across different markets or exchanges. While it helps to stabilize prices, it can also be used for MEV.
4.6.1 Standard Arbitrage
Mechanism: This involves purchasing an asset at a lower price on one exchange and selling it at a higher price on another. This activity helps to equalize prices across markets and is considered a natural part of market operations.
Example: Ethereum is priced at $2000 on Uniswap and $1990 on Sushiswap. An arbitrageur buys ETH on Sushiswap and sells it on Uniswap, pocketing the price difference and contributing to price stability.
4.6.2 Toxic Arbitrage
Mechanism: This occurs when arbitrage opportunities are created by manipulating transaction order, particularly through front-running. It involves rearranging transactions to artificially create price discrepancies that are then exploited.
Example: A searcher manipulates the transaction order to create an artificial price imbalance and then profits by exploiting this discrepancy, causing harm to users whose transactions led to the opportunity.
4.6.3 JIT Arbitrage (Just in Time)
Mechanism: JIT arbitrage involves responding to large swaps detected in the mempool by positioning liquidity to exploit the resulting price changes. This requires rapid execution and liquidity management.
Example: A searcher notices a large swap in the mempool and quickly approves a stablecoin, adds liquidity, executes the swap, and then removes the liquidity to benefit from the price movement caused by the swap.
4.6.4 Rebase Arbitrage
Mechanism: This strategy focuses on taking advantage of price changes resulting from oracle updates or rebases. It involves positioning transactions around these events to exploit the new market state.
Example: The arbitrageur places transactions before and after an oracle update to capitalize on changes in asset values caused by the update.
4.6.5 Cross-Chain Arbitrage
Mechanism: Cross-chain arbitrage involves exploiting price discrepancies for assets across different blockchain networks or between on-chain and off-chain exchanges. This field is expanding with the growing number of chains and assets.
Example: Buying wrapped Ethereum on one blockchain at a lower price and selling it on another where it is priced higher, leveraging differences across chains or networks.
4.7 Liquidations
Liquidations occur when the collateral for a loan falls below the required threshold, leading to the automatic liquidation of the collateral. Participants can then acquire this collateral at a discounted rate.
4.7.1 Standard Liquidations
Mechanism: When a loan becomes under-collateralized due to falling asset prices, the collateral is liquidated. Participants can purchase the liquidated collateral at a discount and sell it at a higher price, often using arbitrage strategies.
Example: A borrower’s loan is collateralized with ETH. If ETH’s price drops significantly, the loan is liquidated. A participant buys the collateral at a discount and sells it at a higher price, making a profit from the price difference.
4.7.2 Toxic Liquidations
Mechanism: This involves censoring transactions that attempt to prevent liquidation, ensuring that the liquidation occurs and allowing the attacker to buy the collateral at a discounted price.
Example: A trader attempts to re-collateralize their loan to avoid liquidation, but the transaction is censored. This results in the loan being liquidated, and the attacker can acquire the collateral at a lower price.
5. Strategies for Mitigating MEV Exploitation
5.1 Flashbots
Flashbots is an organization dedicated to addressing the negative effects of MEV through research and the development of tools. One of its key contributions is the Flashbots Auction, which allows miners to extract MEV in a more transparent and controlled manner. This auction mechanism enables users to submit their transactions with specific instructions on how they should be included in a block, thus reducing the opportunities for unfair MEV extraction. By promoting transparency and fairness, Flashbots aims to mitigate the impact of MEV on users and create a more equitable environment within the blockchain ecosystem.
5.2 Private Transaction Pools and Transaction Ordering Protocols
Private transaction pools limit access to the mempool, restricting who can view and interact with transactions before they are included in a block. This can reduce the opportunities for MEV exploitation by preventing miners from observing and manipulating transactions in advance. Additionally, transaction ordering protocols such as Ethereum’s EIP-1559 aim to improve the efficiency and fairness of transaction processing. EIP-1559 introduces a base fee mechanism that adjusts dynamically based on network demand, thereby reducing the incentives for miners to engage in MEV activities and promoting a more stable transaction fee market.
5.3 Blockchain Design Improvements
Innovations in blockchain design, such as improved consensus mechanisms and economic models, can help mitigate MEV risks. For example, protocols that incorporate mechanisms for fair transaction ordering or incentivize validators to act honestly can reduce the likelihood of MEV exploitation. Enhanced transparency in transaction processing and more robust economic incentives for validators to prioritize network integrity over short-term gains can also contribute to reducing MEV-related issues.
6. Strategies to Address Post-Merge MEV Challenges
To mitigate the negative impact of MEV in the PoS environment, several strategies have been proposed and implemented:
6.1 Proposer-Builder Separation (PBS)
This strategy involves separating the roles of block proposers and block builders. In the PBS model, block builders are specialized entities responsible for creating transaction bundles and constructing blocks, while validators (proposers) select blocks based on bids from builders. This separation aims to reduce MEV centralization by preventing any single party from having undue control over transaction ordering. By creating an auction market for block space, PBS promotes a more equitable system. Builders, who run resource-intensive operations to capture MEV opportunities, submit their bids to validators. Validators choose the most profitable bundles, thus reducing the direct influence of validators on MEV and diminishing the threat of time-bandit attacks.
6.2 Builder API
The Builder API is a temporary solution that facilitates interaction between validators and block builders. It provides a controlled environment for submitting transaction bundles and constructing blocks. Validators use the Builder API to request execution payloads and receive bids from builders, selecting the highest bid for inclusion in the block. This system aims to democratize access to MEV opportunities by lowering the entry barriers for validators and increasing competition among builders. By using commit-reveal schemes, the Builder API reduces trust assumptions and enhances transparency in transaction processing. Projects like MEV Boost build upon this API to offer additional features, such as transaction privacy, which helps mitigate front-running and sandwich attacks.
7. Current MEV Supply Chain
The current MEV supply chain involves various stakeholders, including miners, validators, traders, and developers. Each participant interacts with the transaction pool and the blockchain protocol differently, influencing MEV extraction and mitigation efforts. Miners and validators play a key role in selecting and ordering transactions, while traders and developers contribute to the creation of complex financial products and trading strategies that can be affected by MEV. Understanding the roles and interactions within this supply chain is crucial for addressing MEV challenges and developing effective solutions.
8. Future of MEV
The future of MEV will likely be shaped by ongoing research, technological advancements, and protocol changes. Innovations such as improved consensus mechanisms, more effective MEV mitigation strategies, and updates to blockchain design will continue to evolve the landscape of MEV. As the blockchain ecosystem grows and adapts, addressing MEV will remain a critical focus to ensure a fair and equitable system for all participants.
9. Conclusion
MEV is a complex and evolving aspect of blockchain technology with significant implications for fairness, efficiency, and trust within decentralized systems. While MEV presents opportunities for profit and market efficiency, it also poses challenges related to unfair practices and increased transaction costs. Addressing MEV through innovative solutions, protocol upgrades, and community-driven efforts is essential for maintaining a balanced and trustworthy blockchain ecosystem.